With the rapid development of quantum computing technology, the field of traditional cryptography is facing unprecedented challenges. The public key cryptographic algorithms that we once thought were impenetrable, such as RSA and ECC, have been shown to be vulnerable to quantum computers. As a result, research into cryptographic algorithms that can withstand quantum attacks(Post-Quantum Cryptography, PQC) has become critical for industries that require extremely high security. In this field, the Kyber algorithm, which is notable for its lattice-theory-based design, has been recommended by the National Institute of Standards and Technology (NIST) as an effective Post-Quantum KEM(Key Encapsulation Mechanism) algorithm designed to withstand attacks by quantum computers.
What is NIST’s PQC Competition?
The Post-Quantum Cryptography (PQC) competition, initiated by the National Institute of Standards and Technology (NIST), aims to identify cryptographic standards that can withstand quantum computing attacks in the future. This competition began in 2016, and after years of evaluation, four algorithms were selected for their quantum-resistance capabilities, ensuring that information security will remain effective in the quantum era. On August 13, 2024, NIST announced three PQC standards as follows:
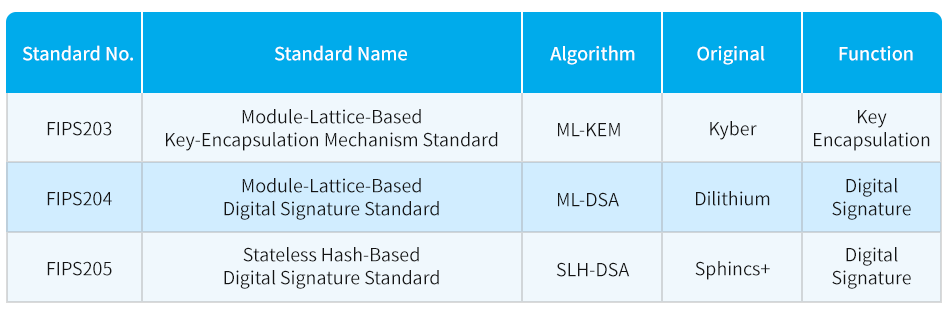
The draft standard for the fourth algorithm, FALCON, is expected to be released by the end of 2024 and will receive final approval in 2025.
What is the Kyber Algorithm?
Kyber is a lattice-based post-quantum cryptographic algorithm mainly used for Key Encapsulation Mechanism (KEM), which securely generates and exchanges symmetric keys. It is suitable for scenarios such as key agreement in encrypted communication, ensuring the security of data transmission even in the presence of quantum computers.
Why is Kyber So Important?
Quantum computers possess powerful computational capabilities that can rapidly break current asymmetric encryption algorithms such as RSA, ECDSA, and SM2. Kyber, by utilizing the complex Learning with Errors (LWE) problem, provides secure data protection in the quantum era and is currently the only standardized key encapsulation algorithm.
How Does the Kyber Algorithm Work?
Kyber is based on the Modular Learning with Errors (MLWE) problem, which implements key encapsulation. This allows two parties to establish a shared key over a public channel. The shared key established securely through Kyber can then be combined with symmetric encryption algorithms to perform encryption and decryption functions in secure communication.
What Are the Advantages of the Kyber Algorithm?
Kyber ensures data security even in the quantum computing era.
Compared to other post-quantum algorithms, Kyber performs well in key generation,
encryption, and decryption, making it suitable for practical applications.
Kyber has been standardized by NIST and is being adopted globally.
What Are the Parameter Sizes for the Kyber Algorithm?
Compared to traditional asymmetric encryption algorithms, Kyber uses larger parameters. The standardized Kyber algorithm has three parameter sets: ML-KEM-512, ML-KEM-768, and ML-KEM-1024, corresponding to security levels 1, 3, and 5, respectively. The public and private key sizes and ciphertext sizes for these parameter sets are shown below. Although the larger parameter sizes may impose some load on the system, they provide the necessary security guarantees in the quantum computing era.
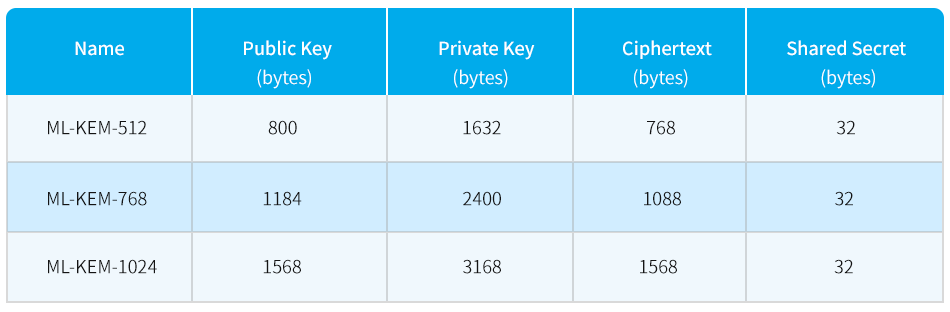
Kyber is a critical step toward the post-quantum era. As the technology becomes standardized and widespread, Kyber will become a key component of the global security infrastructure in the future.
Watchdata, with three decades of specialization in data security, provides comprehensive security solutions built on our extensive expertise in cryptographic algorithms, digital security protection, and secure chip operating system technologies. Our product portfolio encompasses core functions such as authentication, key management, secure storage, and data encryption, fully addressing the security requirements across various scenarios, including connectivity, payment, identities, and digital infrastructures. As we prepare for the future, our product design strategy thoroughly considers the security challenges posed by the era of quantum computing. We are committed to delivering advanced Post-Quantum Cryptography algorithm support to help build a robust digital security protection system for our customers.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文

