Identity authentication is the process of confirming the identity of an entity, involving different entities such as people, machines, objects, system platforms, programs, processes. The following is an overview of these entity authentication methods.
User Authentication
▌There are three main ways to authenticate user identity:
Strong authentication requires a combination of any two methods, known as two-factor authentication, including knowledge, possession, and inherence. Using only biometric recognition cannot provide strong identity authentication.
▌ Comparison of user authentication methods:
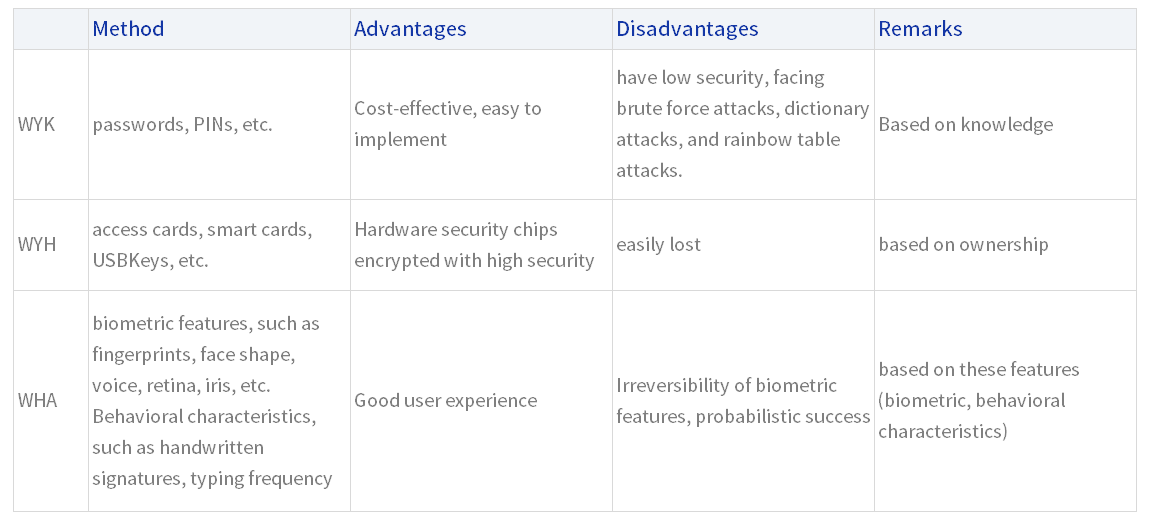
▌ Example of User Identity Authentication Method:
1. Password based authentication:
Users register their username and password, and the system stores the username and password (or the HASH value of the password). When logging in, the system verifies the entered password or the timestamp encrypted with the password.
2. Smart card based authentication:
Implement two-factor authentication, where the smart card stores a public-private key pair representing the user’s identity. When logging in, the private key is used to calculate a digital signature based on a random number digest value, and the system verifies the digital signature.
3. Biometric authentication:
Biometric technology confirms identity by analyzing a person’s unique physiological or behavioral characteristics. Physiological biometric recognition is’ what you are ‘, while behavioral biometric recognition is’ what you do’. Biometric recognition faces issues of irreversibility and linkability, and under generative artificial intelligence technology, being impersonated by large models and having identities misused is the biggest crisis.
Machine Identity Authentication
Machine identity authentication methods include “challenge response” and digital signatures.
1. “Challenge Response” mechanism:
Both parties in communication share the key k. Entity A generates a random number and sends it to B. B encrypts the random number with the shared key and sends it back to A. A decrypts and compares the random numbers to see if they match. This mechanism can effectively resist replay attacks and many other impersonation attacks, and the randomness of the challenge is crucial for security.
2. Digital Signature:
The signer performs cryptographic operations on the data hash value using the private key, while the verifier verifies the digital signature using the signer’s public key. Digital signatures can achieve data integrity, signer identity authenticity, and non repudiation of signature behavior. The message authentication code (MAC) mechanism of symmetric keys cannot achieve non repudiation.
Identity Authentication for Restricted Devices
Object (restricted device) identity authentication emphasizes lightweight and resource limited characteristics, with the aim of ensuring secure and reliable data transmission and identifying data sources. Lightweight authentication features include: fewer data interactions between both parties, smaller data volume, fewer encryption algorithm operations, and the use of identity based signatures, hidden certificates, lightweight message authentication codes with keys, and other mechanisms. Its security is lower compared to traditional identity authentication protocols, but it is sufficient to deal with common attacks on IoT sensing nodes.
Virtual Entity (program, process) Identity Authentication
The purpose of virtual entity identity authentication is to prove that server software, programs, and processes are the software claimed at the time of official release, and to prevent attacks such as phishing and data source fraud. Generally, digital signatures are used for identity authentication to ensure the authenticity and reliability of the servers accessed by users.
Attack and Protection against Multi-Factor Identity Authentication
Research has shown that multi-factor authentication (MFA) can limit the ability of malicious actors to use leaked credentials for initial network access, but MFA with low security still poses risks. Low security MFA includes SMS or voice MFA (which can be easily tricked into transferring phone number control or obtaining verification codes through malicious website links) and MFA that does not support FIDO or PKI (which can be easily cracked by malicious actors who have leaked legitimate credentials). The measure to protect login credentials is to implement MFA based on FIDO or PKI, which can resist phishing and related threats.
With the rapid development of artificial intelligence and quantum computers, identity security is facing more severe challenges. Beijing Watchdata Co., Ltd. has over 30 years of experience in the field of identity authentication. Its smart cards, smart password keys, and other products use advanced encryption technology to ensure the security of user identity information, and are widely used in transportation, finance, healthcare, government and enterprise industries.
For IoT authentication, Watchdata’s lightweight mechanisms are tailored for resource-constrained environments, ensuring secure device communication. Its digital signature technology reliably supports virtual entity authentication, effectively mitigating phishing and data fraud risks.
With innovative technology and high-quality service, Watchdata has won market recognition and customer trust. In the face of new development trends, we actively plan to research anti quantum attack algorithms, explore AI enabled identity authentication, enhance intelligence level, optimize user experience, and continue to build a strong security line for identity authentication in the digital age.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文

