Information security plays a core role in today’s social relationships. It not only safeguards individual privacy and rights but promotes the establishment of social trust and order. It also plays a crucial role in achieving fair distribution of resources, maintaining social stability, and promoting economic development. It has a profound impact on building a harmonious society and cultural heritage.
The fundamental aspect of information security is to prevent resource leakage or unauthorized modification by controlling how information resources are accessed.
What is access control?
Access control is a security measure that controls users and systems to communicate and interact with other systems and resources. It can protect the system and resources from unauthorized access and authorize the level of access after authentication is passed. The entities that access resources and information include various types of entities such as users, programs, processes, systems, terminals, etc.
Access is a form of information transmission between the subject and the object. The so-called subject is an active entity that requests access to objects or data in the object, such as users, programs, processes, etc. that can access information. The so-called object is a passive entity that contains the accessed information, such as a computer, a database, a file, a program, etc. Access control enables users to control, restrict, monitor, and protect resource availability, integrity, and confidentiality.
CIA Security Principles
Confidentiality is the protection of information from unauthorized entities. The access control mechanism needs to specify who can access the data and what operations can be performed on the data, and these activities need to be controlled, audited, and monitored.
The information must be accurate and complete and cannot be modified without authorization. If a security mechanism provides integrity, it will protect data from unauthorized modifications or issue a warning if illegal modifications occur. For example, mechanisms such as hash algorithms, digital signatures, and message verification codes can achieve information integrity protection.
Information, systems, and resources must be able to ensure user usage over time so as not to affect work progress. Generally, fault tolerance and recovery mechanisms are adopted.
Identity and authentication
In the information world, identity is an identifier that distinguishes an entity from other entities. Identity has uniqueness within a certain range. Identity can identify a user, a machine, an object, some virtual entities, etc.
Identity authentication, also known as “identity verification” or “identity authentication,” refers to the process of confirming the identity of an entity in a computer or network or the process of confirming who the entity on the other end of the communication is, to confirm whether the entity has access and usage permissions for a certain resource so that access policies can be reliably and effectively executed.
User identity authentication requires the user to prove to the system that they are the person they claim to be.
The identity authentication of machines, objects, and virtual entities, also known as entity authentication, mainly refers to proving to the other end of the communication that it is the claimed device, data source authentication.
The role of identity authentication:
• Prevent attackers from impersonating legitimate users to gain access to resources
• Ensure system and data security
• Ensure the legitimate interests of authorized visitors
The relationship between access control and identity authentication
Users must prove that they are the person they claim to be, possess credentials, and have been granted specific permissions to complete a particular operation in order to access a specific type of resource. Once these steps are successful, the user can access and use resources, but their activities still need to be tracked and their behavior audited.
Identification is a method of ensuring that a subject is the entity it claims to be. Some proof can confirm identification, such as a username or account. For proper identity authentication, users must provide further credentials such as passwords, PINs, biometric features, or tokens. If it matches, then the subject has passed identity authentication.
Next, the system needs to determine whether this entity has the appropriate permissions to complete the operation it is about to perform. If the subject can access the resource, then the subject is authorized.
The behavior of a subject within a system or domain should be accountable, meaning that the subject can be uniquely identified and their actions recorded.
The four steps of identification, authentication, authorization, and accountability must all occur before the subject can access the object.
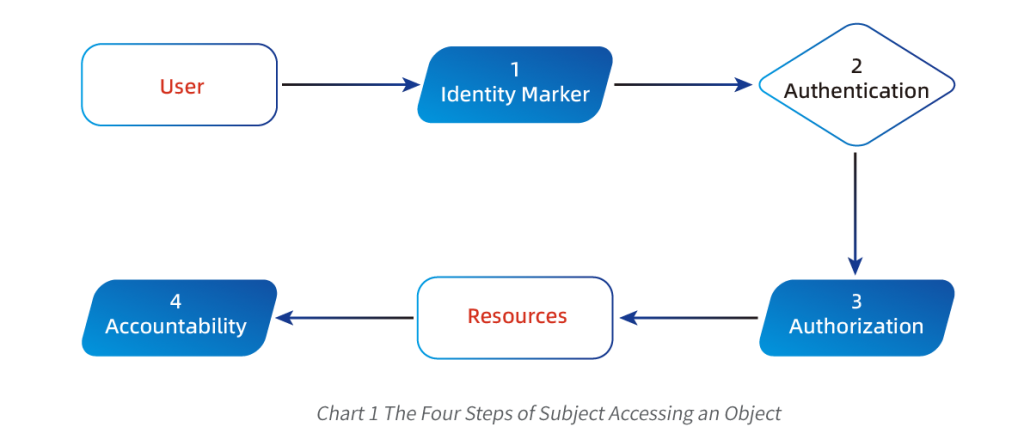
There are three ways for users to authenticate their identity: what they know, what they have, and what features they bring. That is to say, authentication is based on knowledge, authentication is based on ownership, and authentication is based on features (biological characteristics, behavioral characteristics).
Authorization: Authentication and authorization are two essential steps that verify a user’s access to a resource. The first step, identity authentication, requires the user to prove their identity to the system. The second step involves the system confirming whether the user is authorized to access the resource and determining what actions they are permitted to perform on it.
Thirty years ago, with the rapid development of the Internet, information security encountered unprecedented challenges. At this critical moment, Watchdata came into being and began to try to achieve effective authentication with public key system. From the “Great Wall Card Network Authorization System” developed for Bank of China in 1995 to the TGoMOS® Open Multi Application Security Operating System launched in 2021; From PKI USB first generation key to a series of FIDO hardware security key products; Based on password algorithm application technology, digital security protection technology, and secure chip operating system technology, Watchdata provides a series of software and hardware products and services for global user identity authentication.
Users can quickly and securely complete login authentication by using PKI based smart password key products and connecting to terminal devices such as computers and mobile phones through USB interfaces or Bluetooth. At present, the FIDO series products and PKI based intelligent password key products of Watchdata have obtained the second level certificate of password module issued by the National Commercial Password Testing Center and the FIPS 104-3 Level 2 certification issued by NIST in the United States. These products can effectively prevent security attacks and ensure the security of user identity authentication.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文

