Transport Layer Security (TLS) is used to protect the privacy and integrity of network communications. With the evolution of network attacks, the Internet Engineering Task Force (IETF) released the TLS 1.3 standard (RFC 8446) in 2018, achieving significant improvements in security, performance, and scalability.
TLS 1.3 delivers great enhancements over TLS 1.2, with three key improvements:
• Retains only high-strength encryption algorithms (such as AES-GCM) and eliminates outdated algorithms with potential risks.
• Mandates forward secrecy, ensuring historical communications remain secure even if the private key is leaked.
• Reduces the handshake process from multiple round-trips to one, and even achieves zero round-trips (0-RTT) in certain scenarios, enabling faster connection establishment.
• Compatible with legacy protocols, supports customizable extension fields, and adapts to diverse scenarios including IoT and mobile payments.
TLS 1.3 supports mutual authentication to ensure the credibility of both communicating parties (taking 1-RTT as an example, the handshake process is as follows):
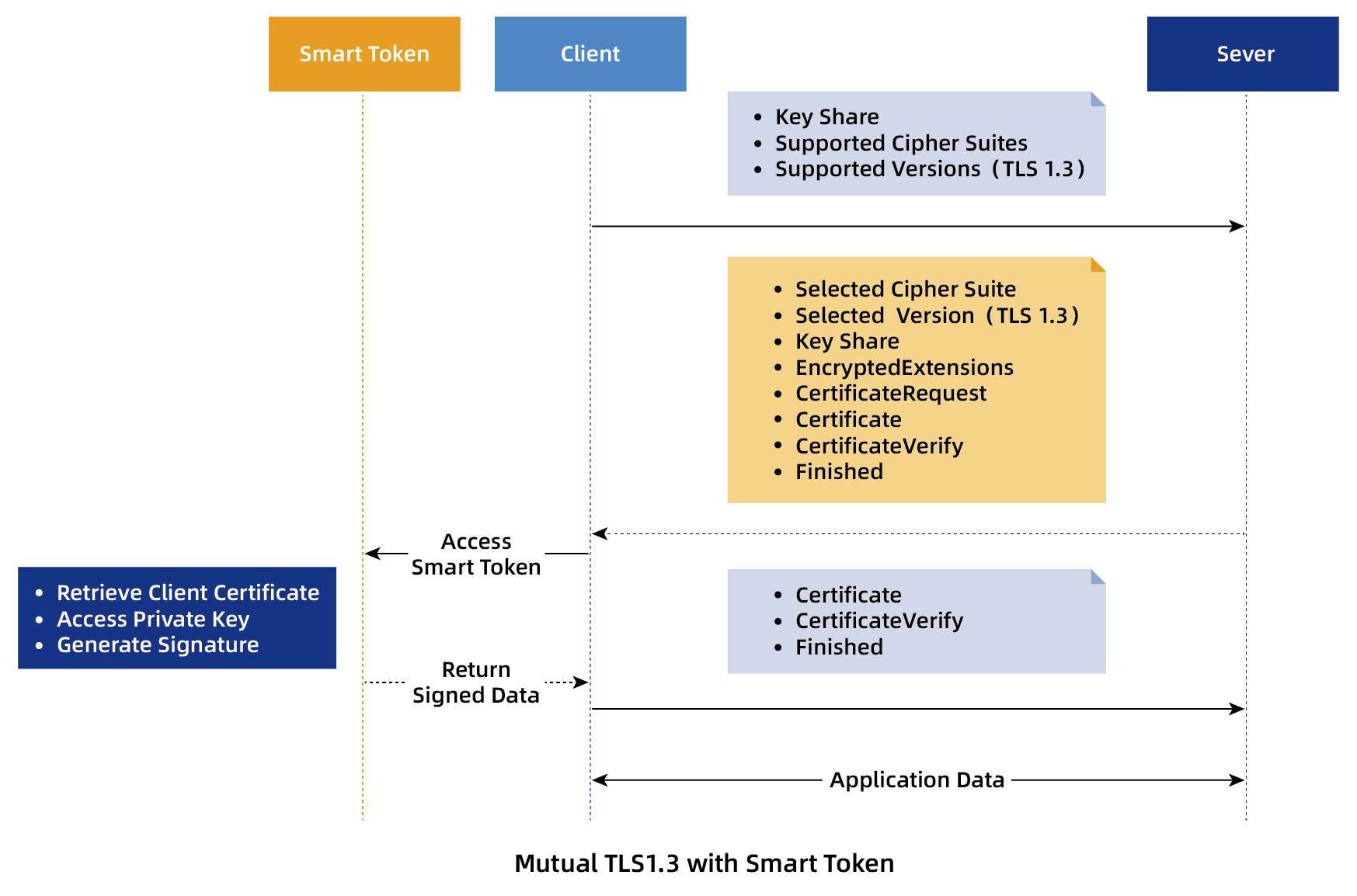
Watchdata’s Smart Token is a hardware device with a built-in secure element. It can store client private keys and perform signature operations. Its core function is to isolate client private keys in hardware to prevent leakage, serving as a critical guarantee for client identity security in TLS mutual authentication. Its key features include:
• Private Key Never Leaves the Device:
Private keys are generated and stored internally in the Smart Token and cannot be exported.
• In-Hardware Signature Execution:
Signature operations are performed within the Smart Token, ensuring private keys are never exposed.
• PIN/Biometric: Authentication Support:
Requires identity verification (e.g., PIN input or biometric scan) for use, preventing unauthorized access.
In TLS 1.3 mutual authentication, Smart Token is typically used for private key signing:
• Certificate Download Phase:
Users generate client key pairs (public and private keys) in the Smart Token via the corresponding soft management middleware. The public key is submitted to a Certificate Authority (CA) for certificate application, and the issued certificate is written into the Smart Token.
• Handshake Phase:
When the client needs to provide a certificate, it reads the certificate from the Smart Token. During the CertificateVerify phase, the client application (browser/client software) sends the handshake message digest to the Token via PKCS11 or CSP interfaces. After the user authorizes access by entering a PIN, the Token signs the digest with the internal private key and returns the signature result to the client, which then forwards it to the server.
With its high security and low latency, TLS 1.3 is widely used in the following scenarios:
TLS 1.3, with its high security and low latency, has become the preferred protocol for modern network communications. Combined with the hardware-level protection of Watchdata’s Smart Token, the mutual authentication mechanism provides reliable security guarantees for high-security scenarios such as finance and government affairs, serving as a key component in building a trusted network environment.
With over 30 years of experience in digital identity authentication and data security, Watchdata has leveraged long-term technical accumulation and industry practice to develop Smart Token products with excellent security and stability. These products have supported clients in multiple industries, including finance, government, and enterprises. We look forward to collaborating with more partners to jointly promote the development of the digital security ecosystem and provide reliable guarantees for Internet identity security.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文

