In March 2025, the U.S. National Institute of Standards and Technology (NIST) released the initial public draft of its white paper titled Considerations for Achieving Crypto Agility: Strategies and Practices (CSWP 39 IPD). This influential publication addresses one of the core challenges facing future cybersecurity infrastructures: cryptographic algorithms will inevitably become obsolete. Therefore, ensuring “smooth migration” and “system resilience” has become a pressing need for modern information systems.
In simple terms, crypto agility refers to the ability to quickly and reliably replace cryptographic algorithms. This capability ensures that systems can respond promptly and maintain protection when facing emerging attack methods, such as those enabled by quantum computing.
For example:
• SHA-1 was found to have security weaknesses as early as 2005, yet many systems still have not fully phased it out today.
• 3DES was not officially deprecated until 2024, despite its successor AES being released as early as 2001.
These cases highlight the high cost of cryptographic migration. In the absence of agility, the prolonged use of outdated algorithms can pose systemic risks.
The concept of crypto agility is not new. As early as 2016, NIST defined three core capabilities that a cryptographically agile system should possess:
• The ability for a device to select its security algorithm in real-time based on its composite security functions;
• The ability to add new cryptographic features or algorithms to existing hardware or software to enhance security;
• The ability to gracefully retire cryptographic systems that have become weak or obsolete.
In the 2025 CSWP 39 white paper, crypto agility is further refined and viewed through the lens of national cybersecurity strategy. The updated definition emphasizes practical system deployment and highlights:
Crypto agility is the capability to rapidly replace or adjust cryptographic algorithms without disrupting system operations, thereby adapting to new security requirements and computing environments and enhancing overall system resiliency.
The white paper summarizes pain points from several historical transitions of cryptographic algorithms, including:
• Long period for a transition: For instance, it took 23 years to migrate from 3DES to AES, demonstrating that without agility mechanisms, upgrades can be extremely difficult;
• Backward compatibility and interoperability challenges: Weak algorithms often need to be maintained for compatibility, which significantly delays their deprecation;
• Constant needs of transition: As computing power increases, algorithm parameters (e.g., RSA key lengths) must be continuously enhanced—and systems must eventually migrate to post-quantum algorithms, requiring long-term evolution capabilities;
• Resource and performance challenges: Newer algorithms—especially post-quantum algorithms—tend to be more resource-intensive, with significantly larger key and signature sizes and greater computational costs.
These challenges show that crypto agility is not simply about replacing algorithms; it must be planned from the architectural level in advance.
1. Protocol Design: Support Negotiation and Transition Mechanisms
The white paper points out that achieving agility at the protocol level requires support for algorithm identifiers and flexible negotiation mechanisms to avoid compatibility issues caused by hardcoded algorithms. It also stresses the need to protect the integrity of the negotiation process to prevent downgrade attacks.
In addition, NIST notes that some standards developing organizations (SDOs) are exploring hybrid algorithms as a transitional solution for migrating to post-quantum cryptography. This approach combines traditional public key algorithms with post-quantum algorithms to provide redundancy during the transition period. Hybrid algorithms can be implemented via single-certificate or dual-certificate structures and leave room for future full migration to PQC.
2. Software Architecture: Modular API Interface Design
Applications should not call specific cryptographic algorithms directly. Instead, they should access cryptographic services via standardized APIs provided by cryptographic libraries. This way, updating an algorithm or policy only requires modifying the library or configuration, without affecting application logic.
The white paper recommends modular architectures that separate cryptographic operations from application logic, enabling on-demand algorithm loading and dynamic policy configuration.
3. Hardware Support: Built-In Redundancy and Upgradability
Hardware devices such as TPMs, SIM cards, and HSMs should be designed with algorithm updateability in mind. This includes support for multiple hardcoded algorithms, upgradable firmware, and replaceable modules.
For security-critical components that contain immutable validation logic at manufacture time (e.g., code used for secure boot verification), it is essential to choose cryptographic algorithms that are strong enough to remain secure throughout the device’s entire lifecycle—avoiding future trust failures.
4. Governance Strategy: Building an Organizational Crypto Agility Framework
To systematically manage the risks associated with cryptographic change, NIST proposes a Crypto Agility Strategic Plan, which helps organizations improve crypto agility at the governance, identification, management, and execution levels. It consists of five key steps:
• Integrate into governance: Embed crypto agility into the organization’s overall cybersecurity governance framework;
• Build an asset inventory: Identify and map all data assets and system components using cryptography, including software, hardware, and protocols;
• Enhance tooling support: Use management tools with capabilities to detect algorithms and vulnerabilities, enabling automatic discovery, assessment, and monitoring of cryptographic components;
• Establish migration priorities: Identify systems at highest risk and prioritize actions based on business importance and potential vulnerabilities; define performance indicators (KPIs) to track progress;
• Execute and mitigate risks: Update algorithms in migratable systems. For systems lacking agility, apply compensating controls (e.g., zero trust architecture) to manage risk.
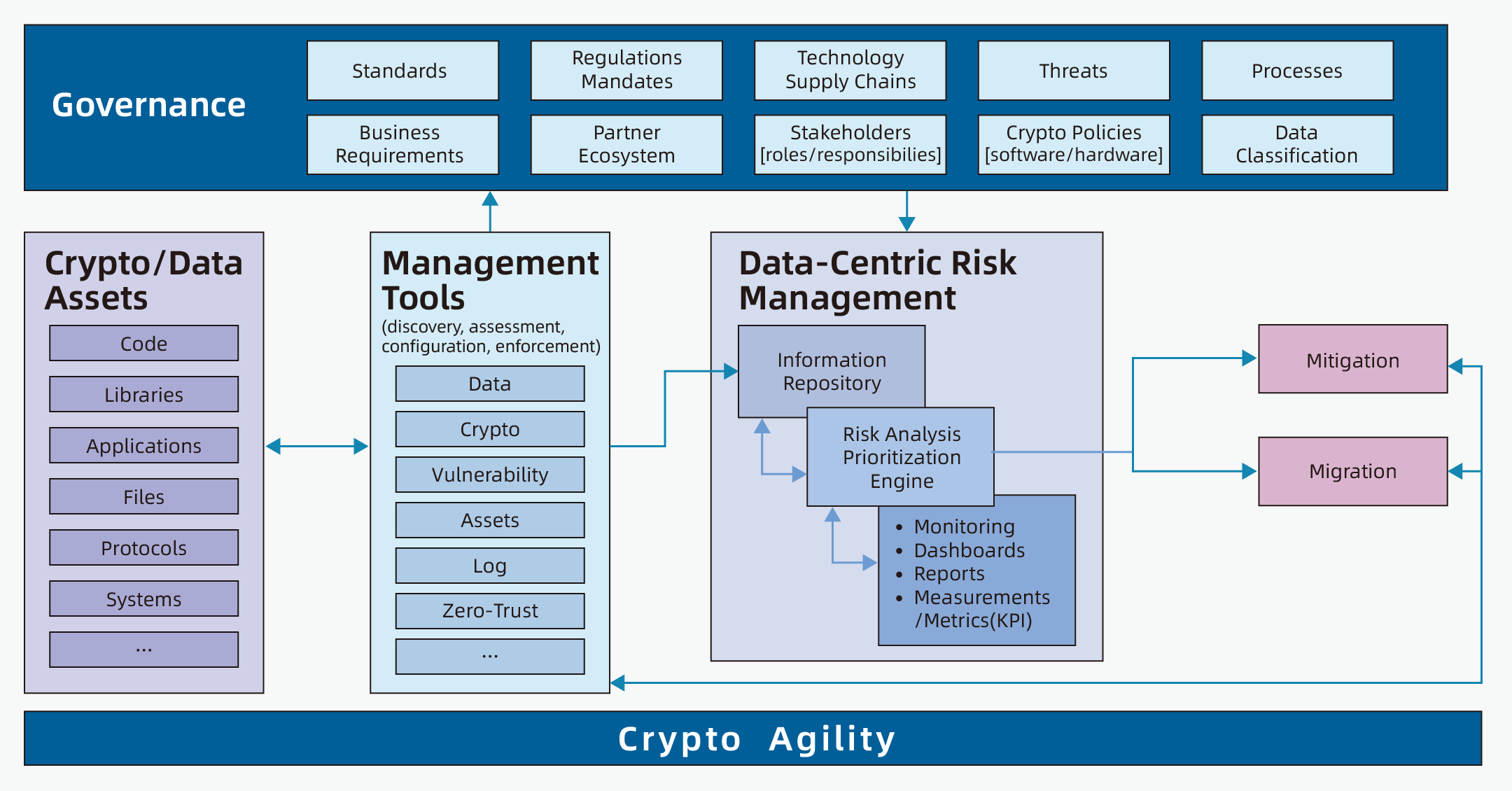
The white paper also emphasizes that these governance actions should be integrated into existing IT management processes and security frameworks—rather than managed separately—to ensure sustainable crypto agility.
At the same time, NIST introduces the Crypto Agility Maturity Model (CAMM), which classifies system capability into five levels (0–4), providing organizations with a reference for self-assessment and improvement.
The evolution of cryptographic algorithms is inevitable. The real question is: Do you have the resilience to keep up?From protocols to hardware, software to organizational policy, crypto agility is becoming a foundational capability of modern digital infrastructure. This white paper by NIST offers the industry a clear roadmap and actionable guidance. As we approach a critical window where post-quantum cryptographic standards are about to be widely adopted, building crypto agility is not just preparation for the future—it’s protection for the present.
As a leading provider of intelligent security technologies and products, Watchdata is deeply committed to innovation in cryptography, secure chips, and identity authentication. We closely monitor global cryptographic standardization efforts—including those from NIST, ISO, and IETF—and actively promote the implementation of crypto-agile architectures across finance, telecommunications, government, and other sectors. Follow us for more insights on cutting-edge technologies and practical solutions.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文