As quantum computing advances rapidly, traditional public-key cryptographic systems face unprecedented threats. Classical algorithms such as RSA and ECC will no longer be secure in the face of quantum computers, reshaping the global information security landscape.
Post-Quantum Cryptography (PQC) has emerged in response and is steadily progressing toward standardization and practical deployment. However, before fully transitioning to PQC, a key challenge remains: how to achieve a secure and smooth migration. This is where hybrid models come into play—providing multi-layered protection by combining classical and post-quantum algorithms, and becoming a widely explored strategy during this transitional phase.
A hybrid model is a transitional security mechanism that introduces post-quantum algorithms alongside classical ones, without drastically altering existing communication structures. It enables stepwise enhancement of quantum resistance.
Typical hybrid mechanisms fall into two main categories, corresponding to the core functions of public-key cryptography:
Hybrid Key Exchange: Simultaneous execution of classical key exchange protocols (e.g., ECDH) and post-quantum key encapsulation mechanisms (e.g., Kyber);
Hybrid Signatures: Applying both classical signature algorithms (e.g., ECDSA) and PQC signature algorithms (e.g., Dilithium) to sign the same message.
These mechanisms are applicable in TLS, VPNs, authentication, code signing, blockchain, IoT security, and other areas. In the current standardization transition period, they offer valuable practical utility. The following sections will detail their design and application.
1. Typical Combination: Kyber + ECDH
Kyber, based on lattice cryptography, has been selected as one of the first PQC standards by NIST for its strong quantum resistance. ECDH, in contrast, is a well-established classical key exchange method widely used in protocols like TLS and VPN.
A typical hybrid approach combines both algorithms as follows:

Advantages of this approach:
• Even if quantum attacks compromise ECDH, Kyber can still provide security;
• If Kyber is attacked before quantum computers are available, ECDH remains a fallback;
• In scenarios with immature standards or hardware constraints, hybrid schemes offer a practical transitional solution.
2. Standardization Support
The IETF has proposed a draft (draft-ietf-tls-hybrid-design-12) supporting hybrid key exchange for TLS 1.3, allowing simultaneous use of two key exchange algorithms during the handshake phase.
3. Protocol Impact Analysis
Using Kyber and ECDH in combination introduces minimal changes to the overall handshake flow, but adjustments are needed in protocol details:
• This approach only supports ephemeral key agreement and cannot replace authenticated key exchange mechanisms;
• Larger handshake data size, which may affect performance on low-bandwidth links or require changes to transport-layer fragmentation;
• Key derivation logic must be clearly defined to securely and consistently combine outputs from both algorithms;
• Increased implementation complexity, especially for constrained devices or lightweight protocol stacks.
1. Typical Combination: Dilithium + ECDSA
In hybrid digital signatures, the typical approach is to generate two signatures over the same message:
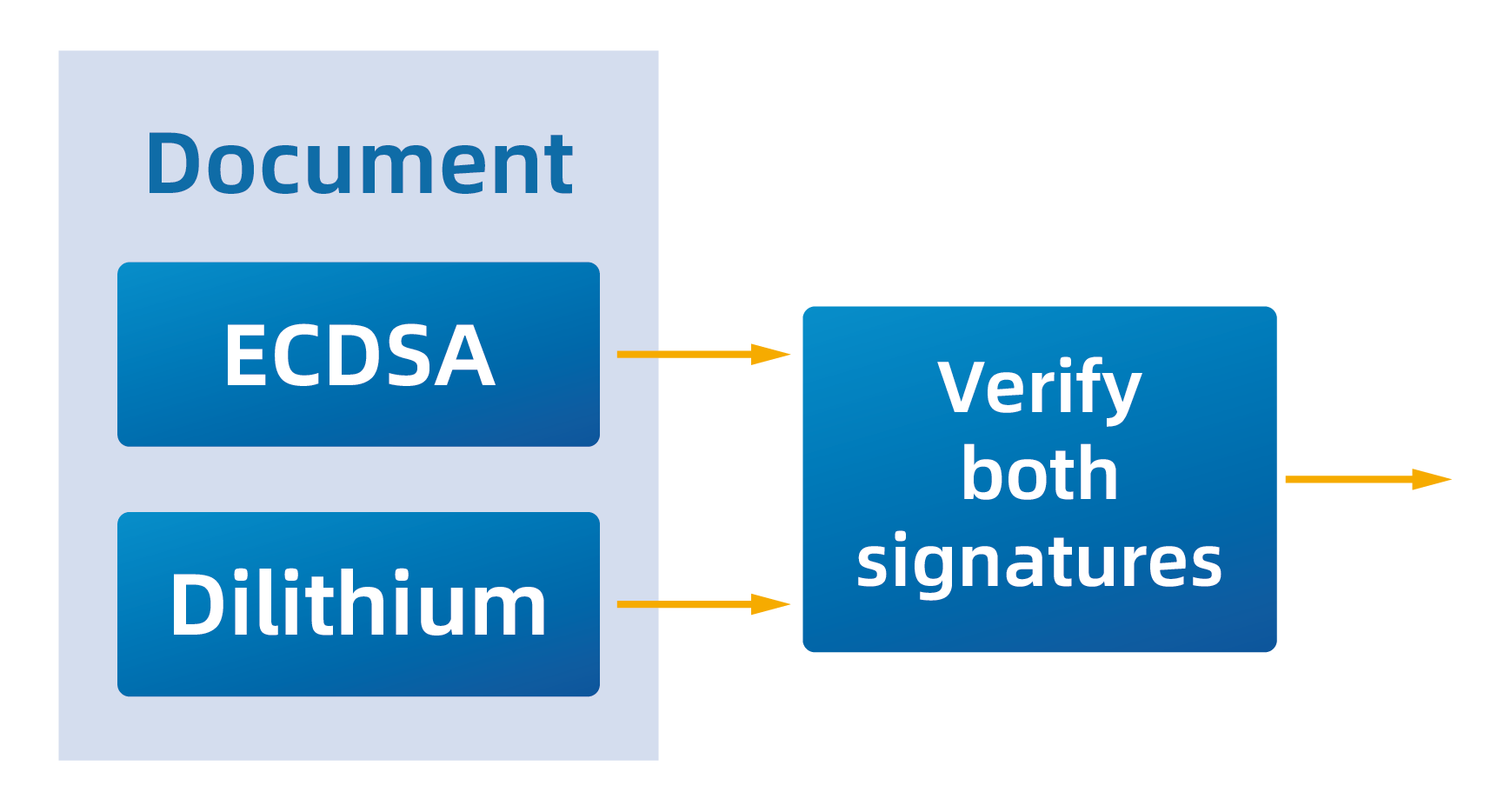
The recipient must verify both signatures for the message to be accepted.
2. Standardization Support
There is no formal IETF draft for hybrid signatures yet, although some working groups have discussed hybrid certificates and multi-algorithm signature formats. Certain open-source communities have already implemented and tested hybrid signature structures.
3. Protocol Impact Analysis
Hybrid signatures introduce several key challenges at the protocol level:
• Increased signature size, affecting transmission efficiency, especially in low-bandwidth or size-sensitive applications;
• Expanded certificate formats, requiring support for dual signatures or composite certificate chains (e.g., X.509, TLS);
• More complex verification logic, as systems must support parsing and validating multiple algorithm types;
• Compatibility and interoperability risks, due to varying implementations of signature structures or certificate handling.
Benefits:
• Redundant security: Enhanced resilience in case one algorithm is compromised;
• Migration-friendly: Provides a gradual path toward quantum-safe infrastructure;
• Flexible deployment: Allows selective use of hybrid techniques based on security level requirements.
Challenges:
• Protocol complexity: Handshake flow, signature structure, and certificates must all be extended;
• Increased resource demands, particularly in embedded or mobile environments;
• Lack of standardized implementations: Deployment approaches vary across the industry;
• Limited long-term viability: As PQC matures, hybrid models may be phased out in favor of full PQC adoption.
The hybrid model serves as a vital bridge between today’s classical cryptosystems and tomorrow’s quantum-safe infrastructure. For industries such as Smart Cards, Secure Chips, Digital Identity, Industrial IoT, and Internet of Vehicles, early adoption of hybrid schemes not only addresses emerging quantum threats but also aligns with evolving compliance requirements.
As PQC algorithms and hardware/software ecosystems mature, systems will gradually migrate toward native quantum-safe architectures. In the meantime, hybrid solutions remain the most practical and feasible transitional approach.
Watchdata has long been dedicated to information security technologies, actively investing in post-quantum cryptography research and its real-world application. We are committed to delivering secure, future-ready cryptographic solutions for industries including finance, government, and IoT.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文