With the rapid advancement of quantum computing, traditional public-key cryptographic algorithms such as RSA and elliptic curve cryptography (ECC) are facing potential security threats. To safeguard critical national information infrastructure, the U.S. National Institute of Standards and Technology (NIST) launched the Post-Quantum Cryptography (PQC) Standardization Process in 2016, aiming to select a new generation of encryption standards resistant to quantum attacks.
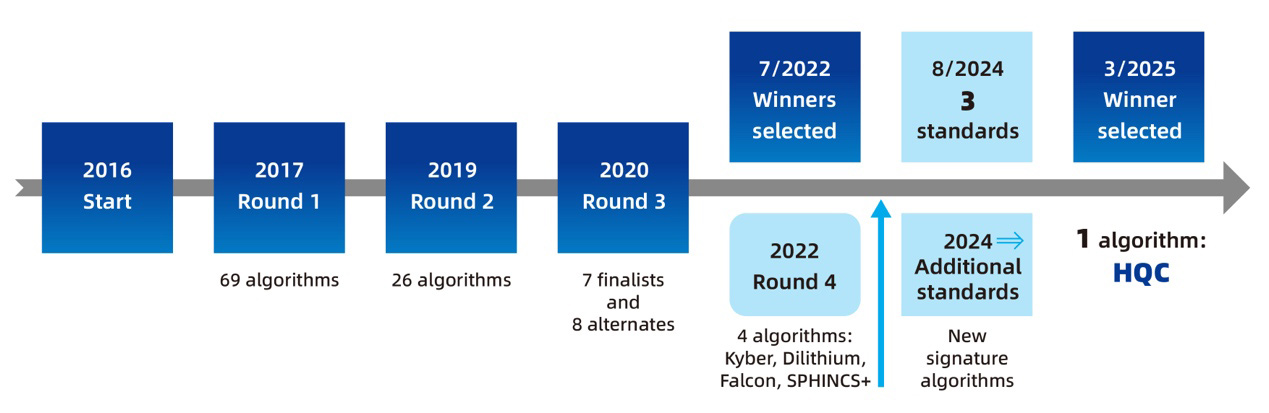
Figure 1: NIST PQC Standardization Process Timeline
In 2022, NIST selected its first group of standard algorithms, including the lattice-based key encapsulation mechanism (KEM) Kyber, the lattice-based digital signatures Dilithium and Falcon, and the stateless hash-based signature SPHINCS+. Kyber, Dilithium, and SPHINCS+ were respectively included in the FIPS 203, 204, and 205 standards released in August 2024, under the names ML-KEM, ML-DSA, and SLH-DSA.
In March 2025, NIST released its official report NIST IR 8545: Status Report on the Fourth Round of the NIST Post-Quantum Cryptography Standardization Process, in which another KEM—HQC (Hamming Quasi-Cyclic)—was selected as a complementary standard to Kyber, further improving the diversity and robustness of the post-quantum cryptographic ecosystem.
The report summarizes the evaluation process of fourth-round KEM candidates, which began in 2022, and officially announces the selection of HQC, a code-based KEM, as the second standard for KEM.
NIST clarified that the goal of the fourth round was to select a KEM based on a mathematical foundation distinct from Kyber (a lattice-based algorithm), in order to enhance overall cryptographic diversity and system resilience to support crypto-agility. The final round of evaluation included HQC, BIKE, Classic McEliece, and SIKE. SIKE was eliminated in 2022 due to practical cryptanalysis.
After a comprehensive review, NIST chose HQC as the new standardization candidate, with an expected draft standard to be released within two years.
According to NIST IR 8545, the selection of HQC was based on the following key factors:
▌ Mature Security and Transparent Structure
HQC’s security is based on the Quasi-Cyclic Syndrome Decoding (QCSD) assumption, a well-studied hard problem in coding theory for over 50 years. It does not rely on any hidden trapdoors, making it suitable for formal verification and theoretical analysis.
To achieve IND-CCA2 security, a sufficiently low decryption failure rate (DFR) must be guaranteed. The report notes that HQC outperforms BIKE in this aspect, as the DFR analysis of BIKE has remained an open problem during the fourth round.
▌ Balanced Size and Performance
Thanks to its quasi-cyclic structure, HQC achieves relatively small public-key and ciphertext sizes, although still noticeably larger than those of lattice-based KEMs. Specifically, HQC’s ciphertext and public key sizes are roughly 2.9 and 1.5 times those of BIKE, respectively. Despite its higher bandwidth, HQC’s key generation and decapsulation are significantly faster than BIKE, with encryption speed being about half that of BIKE.
In contrast, although Classic McEliece provides solid security, its large key sizes limit its practicality in many real-world deployments.
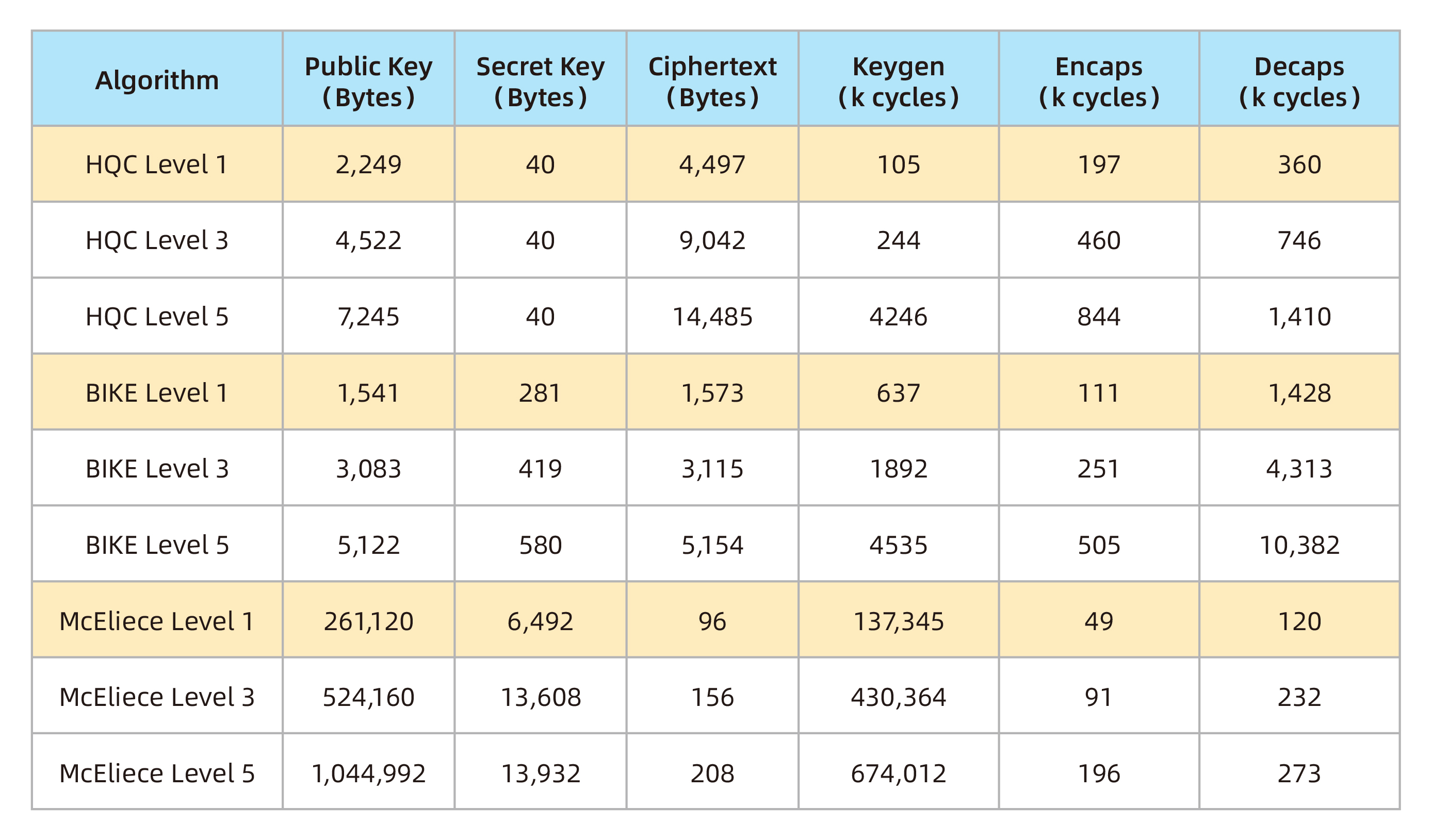
Figure 2: Parameter Size and Performance Comparison of Four Algorithms
▌ Implementation Characteristics
The submitters of HQC indicated two patents that could potentially be relevant to an implementation of HQC. However, the patent owner committed and agreed to grant to any interested party on a worldwide basis a non-exclusive license for the purpose of implementing the standard without compensation and under reasonable terms and conditions that are demonstrably free of any unfair discrimination.
Additionally, while Classic McEliece features small ciphertexts and fast encapsulation and decapsulation performance, making it potentially suitable for use cases where the public key is transmitted only once (e.g., VPNs or file encryption), it is currently under ISO standardization review. Dual standardization by NIST and ISO may cause incompatibilities. NIST may consider adopting the ISO version if it is finalized in the future.
HQC is a code-based key encapsulation mechanism that leverages the structural advantages of quasi-cyclic codes. It does not embed any trapdoors within the code and has a security reduction directly to the QCSD problem, making it a mainstream representative of code-based cryptography.
As with other code-based schemes, the best-known attacks against HQC are based on information set decoding (ISD), which remains the most effective known method to date.
According to NIST’s official positioning, HQC is not intended to replace Kyber but to serve as a complementary solution. Kyber remains the primary, high-performance, broadly compatible KEM, while HQC offers an alternative security foundation.
We evaluated both soft algorithms at Level 1 and Level 3 in our test environment. The following figure summarizes the results:
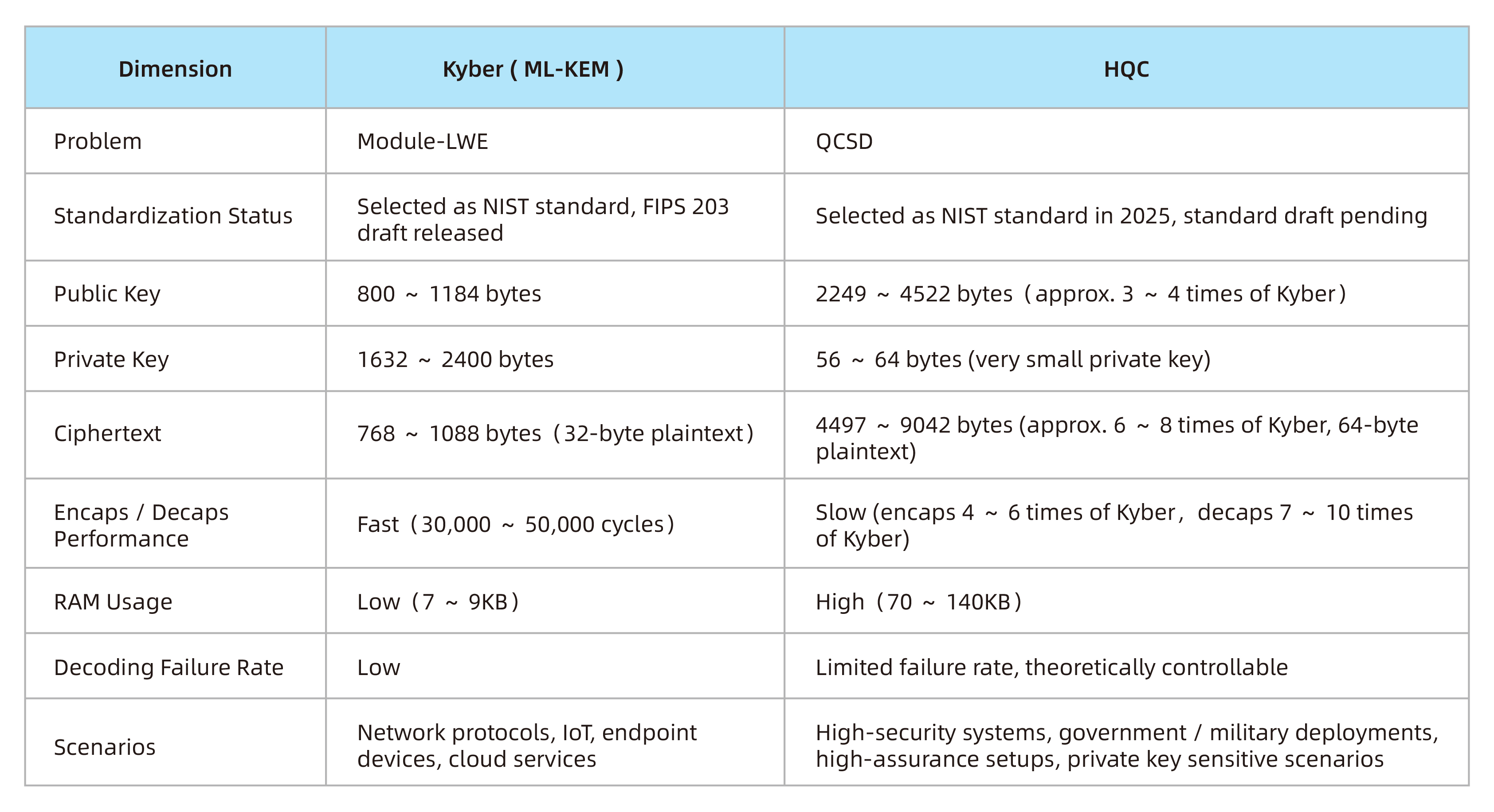
Figure 3: Comparison Between Kyber and HQC
The inclusion of HQC reflects NIST’s emphasis on diversifying the mathematical foundations of post-quantum cryptographic standards. While Kyber remains the mainstream deployment target, HQC offers an alternative path that is particularly suitable for high-security or private-key sensitive environments.
HQC’s draft standard is currently under development and is expected to be released within the next two years. NIST has also announced plans to hold a new post-quantum cryptography conference in September 2025 to further promote the standardization of digital signatures and other schemes.
With over 30 years of deep experience in the information security industry, as industry experts, we deeply understand the importance of standards and regulations for industry development.
Watchdata will continue to monitor the progress of NIST’s PQC standardization efforts and proactively pursue practical deployment opportunities in secure applications.


 English
English Français
Français Español
Español Português
Português 简体中文
简体中文